Loading component...
At a glance
- The world’s almost-overnight move to remote working has brought about several threats to cybersecurity.
- The current breaches are a variation on known forms of cyberattack, but with COVID-19 as a general theme.
- There are tools and options to make devices more secure, and it is vital to guard against distraction when performing routine tasks.
When Australian comedian and radio host Hamish Blake put out a social media call for Zoom logins and passwords so he could engage in some housebound hijinks during the COVID-19 lockdown, the results were swift. Blake got more than a 1000 responses within a few days, and then set about “Zoom-bombing” in on the videoconferencing service – randomly dropping in on people’s work meetings, with predictably amusing results.
While most saw the funny side of him pretending to be everything from a CFO to a primary school teacher, it did bring into focus a rather more serious issue: just how secure is the technology we’re using to work from home?
With a once-in-a-century pandemic sweeping the world, Australians were understandably given very little time to adapt to the new way of working. Australian Prime Minister Scott Morrison brought in a range of social distancing measures on 23 March to help stop the spread of COVID-19, tightened them further two days later and, by the 29th of the month, determined that aside from shopping, exercise and compassionate reasons, people should only leave the house “if you cannot work or learn remotely”.
For millions of people, the occasional work-from- home option suddenly became the five-days-a-week reality. While companies had increasingly adapted to remote and home working for white collar industries, it’s fair to say most weren’t prepared for it on this scale.
The new world order

“It used to be a case of getting up in the morning, driving to work, parking and walking inside – and until that point you’d have no access to corporate data,” says Dr Micheal Axelsen FCPA, senior lecturer, business information systems at the University of Queensland Business School.
“In the last 12 years or so, it has effectively gone from having one workplace where you have most of your people and you’ve got a few people wandering around, to hundreds of workplaces all at home and data flying back and forth with potentially unsecured wi-fi.
"The current situation has intensified that risk dramatically.”
As the impacts of COVID-19 started to ramp up in Australia, with it came the cyberattacks related to the pandemic.
In a six-week period starting a fortnight before lockdown, the Australian Cyber Security Centre (an arm of the Federal Government’s Australian Signals Directorate) received more than 95 cybercrime reports about people losing money or personal information to COVID-19-themed scams and online frauds, responded to 20 cybersecurity incidents affecting COVID-19 response services/major national suppliers, and disrupted over 150 malicious-themed websites pertaining to COVID-19.
Tricks of the trade
In many ways, there’s nothing particularly new about the current breaches and scams; they’re more or less variations of a theme done in a home environment, where there’s usually less impediment to success.
In other words, fewer Nigerian princes and more COVID-19 coercion.
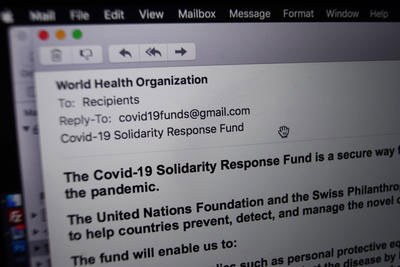
The Australian Competition and Consumer Commission’s Scamwatch website has noted that recent “phishing” (fraudulent digital correspondence sent to extract personal or financial information) hooks have been centred on texts and emails with fake COVID-19 testing links and information.
Scammers are also pretending to be government agencies helping out with applications for financial assistance or payments for staying home, or posting fake job ads and bogus JobSeeker payment links.
Corporates don’t miss out either, with COVID-19- themed phishing for banks, supermarkets and insurers. The information extracted is later used in some type of scam.
Potentially far more dangerous is “spear phishing” – where the perpetrator already has some information about you, your company or clients.
Specifically targeted to a company or individual, spear phishing can also be more convincing, asking for confidential account details or having a link that downloads malware to copy keystrokes from your computer.
Home is where the hack is
“Working from home presents new opportunities for the bad guys, as the network security/endpoint security at home is not as robust as back in the office or within companies,” says Jarret Le Roux, director at Australian Forensics and Investigations.
“We’re seeing home routers and internet modems being targeted. This isn’t new, but we’re seeing an increase in the amount of traffic targeting these devices.”
There is a range of options to make the devices more secure, from using a complex password and changing it regularly, to hiding the network and limiting its range so outsiders can’t access it.
A relative lack of security can dovetail into what may be a looser home environment, too. Le Roux says distracted or bored employees are more inclined to click on dubious links, while devices could be shared with children who can download screensavers or games with hidden nasties.
Sometimes, it can simply be a case of a lack of knowledge but too much access; an employee without an IT professional near them but with an administration password can be a dangerous thing.
The broad solution involves setting limitations as to who can use a computer and what type of work it can be used for, and only using administrator privileges when directed.
“I think particularly for accounting and finance people, we’ve always had to keep our eye on the ball, and it’s really easy to be distracted right now,” Axelsen says.
“Keep an eye on the basics; it’s always the little things that seem so mundane that end up causing us major grief. I’m thinking particularly of phishing exercises or not complying with the JobKeeper [requirements], or getting sucked into a scam.”
CPA Library resource:
Zoom goes boom
With so many workers operating from home, the demand for videoconferencing services has skyrocketed: Microsoft Teams, Google Hangouts and Zoom are among the popular options.
The latter’s growth has exploded, going from an estimated 10 million users at the end of 2019 to 300 million by late April. With it have come some growing pains.
Hamish Blake may have got some laughs with his Zoom-bombing, but most Germans were left horrified when Neo-Nazis hijacked a Holocaust memorial event streamed by the Embassy of Israel in Berlin.
There’s also been a range of phishing scams, where fake Zoom emails direct users to external links where login details can be stolen.
While Zoom has been getting a number of security boosts, Axelsen says like most cyber products, it will still have weaknesses.
Ensuring good password protection, having a savvy host who is cognisant of who is being let into the meeting, judiciously using things like the mute feature, and preventing screen sharing/ saving to the cloud are measures users can take to limit the chances of getting bombed.
“The defaults as always with Zoom are set up more for convenience than for security, so bear that in mind,” he says.
“However, in most instances, you don’t need to panic unless you’re protecting the president or have a major secret that you are sharing.”
Problems in your own backyard
While a large number of scams and cyber security breaches have origins overseas, Dan Weis, senior cyber security specialist at Kiandra IT, says there’s good reason to believe there could be an upswing in domestic-related incidents.
The downturn in economic conditions and related spike in unemployment are expected to give people extra motive, time and a reason to justify their behaviour.
“Disgruntled employees are always an issue. Many incident responses in the past have involved former employees connecting back into company networks, stealing intellectual property and that sort of stuff,” he says.
Often this can be done indirectly, with a former employee passing that information on to someone else or even paying someone on the dark web to instigate the security breach.
Axelsen says much of the mitigation in the first instance can be managed by the employer, starting with terminations that are handled appropriately, and from there having systems in place where access to information and passwords is quickly shut down.
As he puts it: “If you’re burning a bridge, don’t give ex-employees a bridge back into the organisation.”
CPA Australia podcast:
The dos and don'ts of remote working
For employees:
- Don’t reuse passwords across accounts
- Don’t click on links in emails
- Protect your home wi-fi and router
- Know who to report scams to in the company
- If you are handling or processing payments, consider yourself a target for cyber criminals and act accordingly
- Turn on monitoring within your email platform (Office 365, Gmail, etc.)
- Install an Endpoint Detection and Response (EDR) platform
For companies:
- Talk to employees regularly about security. This includes physical and IT security
- Implement two-factor authentication on all accounts
- Ensure all systems are patched/have the latest updates
- Have a proper back-up strategy
- Assume there’ll be IT breaches and have contingency plans for things such as ransomware attacks, network compromises and rogue employee actions
- Segregate your computer network and secure your most important data
- Segregate computers for work and personal use where possible for employees; if a personal device has to be used, set up a new user account on the operating system where possible
- Have sufficient virtual private networks (VPNs) available
- Even in a downturn, avoid deep cuts to IT staff – it may come back to bite you longer term

