Loading component...
At a glance
- As cloud systems become more and more prominent in the workplace, good password practices are increasingly important.
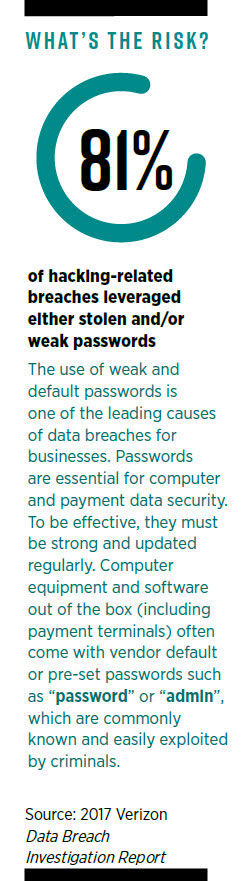
- Weak passwords are the most common cause of data breaches, and promoting good password practices needs to be part of an organisation’s culture.
- Aside from promoting good password practices, password management software and two-factor authentication are useful tools in data security.
By David Walker
By this point, most users of IT systems understand that strong password protection is a foundation requirement of data security. As we use more and more cloud systems, good password practices are becoming ever more important. Security breaches can hamper a firm’s growth, requiring expensive recovery and reporting and eroding the trust of customers and regulators.
However, making these practices part of a firm’s culture can be tough. Accounting firms are busy places, so people will skip difficult steps when they can’t see a pay-off.
As Practice Protect founder Jamie Beresford puts it, you can’t argue with easy.
“People are worried about the deadline for that day,” he says. They aren’t so worried about the long-term risk of their accounting firm being breached.”
If your practice relies at all on cloud-based infrastructure, there are three security practices you need to make part of your culture. That is, you need to ensure that these are used by everyone and ignored by no one.
- Use unique passwords.
- Require password manager use.
- Require two-factor authentication.
Making this happen can be easier said than done.
Cybersecurity is a psychology challenge
Cybersecurity experts now emphasise that changing people’s security behaviours is as much a psychological challenge as anything else.
In a famous 2014 paper, three UK researchers – Maria Bada, Angela Sasse and Jason Nurse – found that “fear appeals” alone typically did not persuade people to adopt good online security. Security campaigns that instructed people on good security practices often didn’t work either, because they demanded more effort and skill than most users possessed.
What does work? The UK researchers and others have since identified several important behaviours.
- Education needs to be aimed at specific users, be actionable and provide feedback to users as they learn.
- Training and feedback need to last until users change their behaviours.
- Strong leadership commitment to security initiatives is needed within businesses.
Set the cyber-tone from the top
Joss Howard, cybersecurity senior advisor at global cybersecurity consultancy NCC Group, stresses above all the importance of leadership in improving cloud sign-in behaviours. Owners, CEOs and boards need to “set the tone from the top” on cybersecurity and explain why “this is good for all of us”.
Security initiatives led by technical staff without high-profile leadership support, on the other hand, are prone to failure.
In addition to leadership support, security initiatives need room to take hold – what Howard calls a grumbling phase – where feedback is invited and where members of the firm raise issues with the signin rules and processes and see that their questions are being taken seriously. Communication at this point can make or break new security plans.
The level and type of complaint and uncertainty will depend on technology skills within the business, Howard notes. In a smaller accountancy firm, she says, some staff may be thinking, “I can barely use Word, let alone do two-factor authentication”.
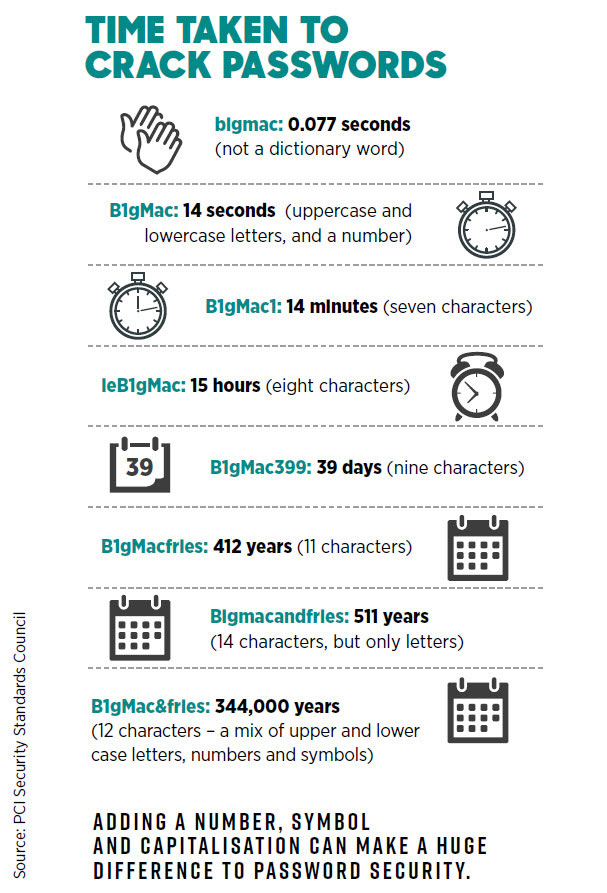
Use unique passwords
Online accounting vendors have helped make accountants early adopters of cloud computing, notes Beresford.
However, it has also worsened a problem that IT specialists call “password daisy-chaining”, where users employ one password across multiple sites. Why do users daisy-chain?
Because they can’t remember 10, or 30, or 100 different passwords. No one can; people often take shortcuts to save time and effort.
The most common shortcut, says Beresford, is using a few different levels of password. Users will typically apply the most cryptic password – dates to which they’re emotionally attached, for example – to their email, their online dating app and their social media profiles, and they may also change these passwords regularly.
For data of less emotional significance – the data in a travel app, for example – users will often apply a much less cryptic, more easily guessed password. Your business’s data, says Beresford, will typically be in that second class of less significant data.
The result can be that anyone who discovers the user’s business Dropbox password also has instant access to their business mail, their Xero account and their Office 365 files.
RSM Australia’s national head of security and privacy risk services, Darren Booth, demonstrates the problem by using a website that checks whether an account is known to have been compromised: haveibeenpwned.com. Its results can be sobering.
If users need to have unique passwords for each site, how do they keep track of them all?
The first response to the too-many-passwords problem was written password lists. Yet those are hard to maintain, hard to use and potentially easily removed from inside a user’s top drawer.
Require password manager use
Password management software emerged as a better solution to this problem. These programs not only keep a list of your passwords, but will often also autofill login screens.
They also have better security than the auto-login systems built into browsers such as Google’s Chrome. Security experts such as Bruce Schneier, a noted consultant and fellow of Harvard’s Kennedy School, argue that password managers are essential in today’s IT environment.
The first generation of these tools was built for consumers: LastPass, 1Password, KeePass and the like. Now a new generation of tools has appeared, designed for corporate use and offering enterprise-level control: CyberArk’s Enterprise Password Vault, Thycotic’s Secret Server, One Identity’s products, Click Studios’ Passwordstate, and LastPass’s Teams and Enterprise are a step up from their consumer products. Booth says such tools are “continuing to gain traction”.
Education is vital: users must be persuaded to use the password protection tool to access the cloud facilities they need.
The usability of these tools has also improved over the past five years, Howard says; some systems do almost everything for users.
Howard stresses that as with other tools, education is vital: users must be persuaded to use the password protection tool to access the cloud facilities they need.
Use two-factor authentication
Two-factor authentication (2FA) demands that users provide something apart from a username and password to access a cloud application. Typically, this “second factor” is a code sent to a user’s mobile phone or, more securely, to a smartphone authenticator app from a firm like Google, Microsoft or LastPass.
The Australian Taxation Office (ATO) now requires that cloud accounting practices – Xero, MYOB, QuickBooks Online and the like – provide 2FA. However, client data also resides in all sorts of non-accounting cloud apps, from online spreadsheets to email, to project management tools. You should aim to protect these with 2FA as well.
Some users will resist having to provide a second authentication factor simply to open their email. You may be able to simplify this by using a hardware security key, such as those sold by Yubico, which can simply be plugged into a desktop every morning.
The good news is that the ATO’s requirements, the use of fingerprint technology in phones and the use of 2FA codes in consumer banking, are all making these techniques more familiar to everyone.
“Users are embracing the technology,” Howard says. Booth says Microsoft’s use of the technology in Office 365 has helped accustom users to using a second factor of authentication.
Bringing security together
An alternative approach to sign-in security is to move most sign-in processes out of the users’ hands altogether.

Technologies known as Identity and Access Management (IAM) are still developing, especially in terms of cloud capabilities. They present many businesses with confusing choices; technology analysis firm TechVision has referred to these as “identity sprawl”.
Yet they all offer businesses the possibility to have users sign in just once and gain access to many of their cloud services – a service called single sign-on, or SSO.
These services also let firms more easily maintain password policies, allow access to users only from certain locations, and sometimes provide additional services such as enforcing 2FA. They generally rely on the cloud service provider, such as Xero or Dropbox, writing software to interoperate with them.
SSO solutions come from major cloud players including Microsoft and Google, as well as independent firms such as Okta, OneLogin and Ping Identity. They let staff access many applications with a single username/password combination. Some products will control 2FA as well. Microsoft Office 365’s built-in capabilities offer basic identity management for users, and Booth says many organisations are currently implementing this system.
Cloud access security brokers (CASBs) such as CipherCloud, Bitglass, Netskope, Microsoft’s Adallom and Cisco’s Cloudlock act as central data authentication hubs, making logins available from a central location and checking on how they’re being used. Many connect to SSO portals and email servers. Tech analysis firm Gartner has forecast that by 2022, 60 per cent of large US businesses will use CASBs, up from 20 per cent at the end of 2018.
Practice Protect is an authentication hub designed for accounting firms and overseen by practice managers, and which can include ongoing staff training. The Password Protect system claims to work with over 50 accounting applications, including Xero, QuickBooks, Salesforce, Dropbox, Office 365 and major banks.
Case study: A password daisychain to disaster
Beresford gives the real-life example of a Townsville accounting firm that had an accountant’s personal password exposed through an infected home computer. Because she was daisychaining passwords, her Office 365 account was quickly compromised. Clients ended up being sent ransomware via an email link; three clients clicked on the link and were infected, and one of the three didn’t have their data backed up.
Worse, says Beresford, the accountant’s professional indemnity insurance didn’t cover them because they didn’t have the required IT and internet usage policy in place.