Loading component...
At a glance
A major data breach at Australian telco Optus earlier this year sent shockwaves through the business world.
Some reports suggest that Optus may have been hacked through an unprotected application programming interface (API) endpoint. An API endpoint gives applications access to resources such as customer data.
For business leaders, the Optus breach is a reminder that any organisation can be breached – sometimes in unexpected ways.
Yet data is often breached through weak, reused passwords, phishing attacks, spreadsheets emailed to the wrong person and other preventable means.
CPA Australia's cyber security hub
The main vulnerabilities
Few breaches are successful due to the skill and persistence of hackers. A report from the World Economic Forum indicates that 95 per cent of cyber security issues can be traced to human error.
“Responsibility for protecting your organisation’s information should be shared among all staff and not left to a single individual or team,” says the federal government’s Australian Cyber Security Centre (ACSC).
Among the recommendations in ACSC’s Small Business Cyber Security Guide:
- Set operating systems and apps to update automatically to minimise software vulnerabilities
- Manage data access, so that employees only have access to what they genuinely need for their work
- Use multi-factor authentication (MFA) on accounts
- Train staff in cyber security basics
Data protection tools

Many tools can be used to protect data and implement the ACSC’s key recommendations.
For instance, a directory management system such as Windows Active Directory allows IT administrators to control access to network folders and files.
Cloud-based directory platforms such as JumpCloud and Okta build on this by offering identity and access management (IAM) with support for single sign-on (SSO) and MFA, so users only log in once a day to use all their apps securely.
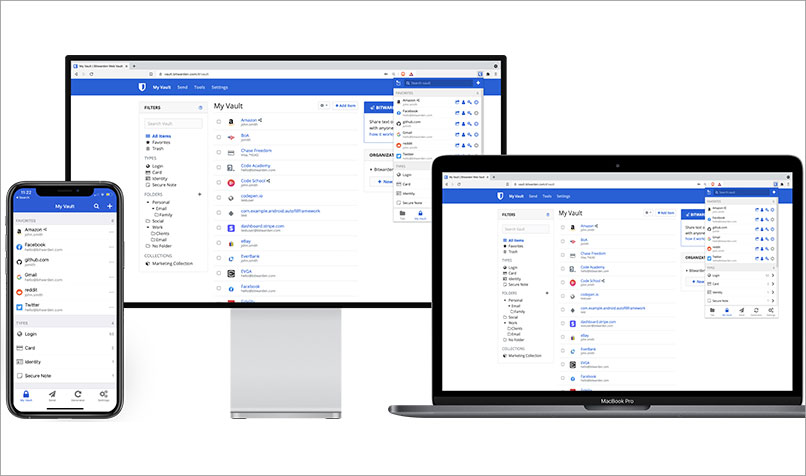
A password manager, such as Bitwarden for Teams, is a simpler option and may suit small businesses wanting to secure employee access credentials. Bitwarden offers MFA and end-to-end encryption.
In terms of training, ESET offers a free 60-minute online course and a paid course that includes a phishing simulator, while KnowBe4 has a vast selection of courses.
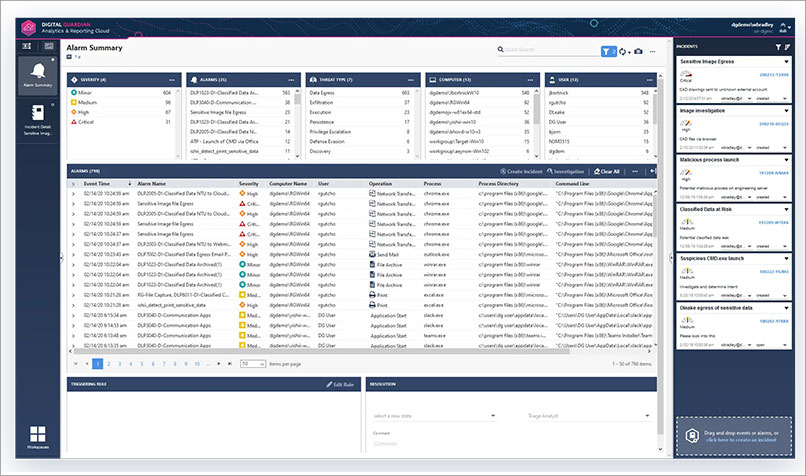
You can also protect your organisation and customers from user errors with a data loss prevention (DLP) solution, such as Digital Guardian. DLP solutions can identify, monitor and prevent sensitive information from being leaked.
Incidence response
The ACSC recommends that organisations implement and regularly review incident response and business continuity plans. The ACSC provides a downloadable cyber incident response plan template and checklist.
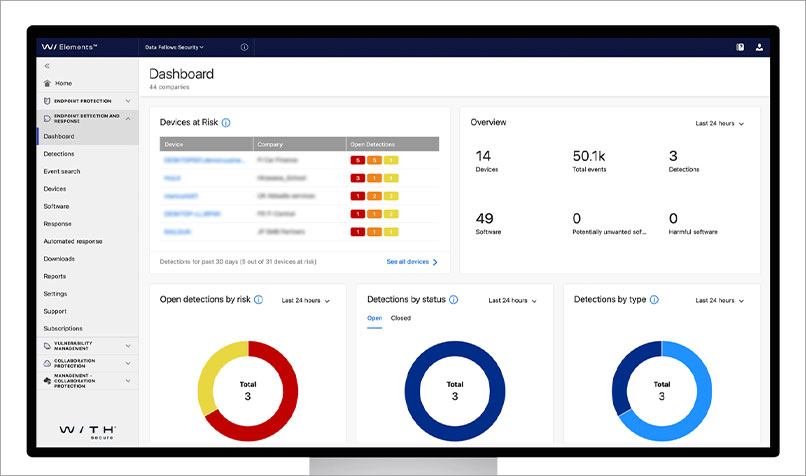
Other tools can help, such as endpoint detection and response (EDR) solutions. These are typically part of endpoint protection suites, such as WithSecure Elements.
An EDR tool uses threat intelligence to monitor employee devices continuously to detect malware and suspicious activity. It responds by automatically cleaning or isolating a system and providing guidance on how to mitigate the threat. Managed detection and response services, such as CrowdStrike, expand on this by offering advice from real people to deal with advanced threats.
Individual protection
For individuals who wish to protect themselves if their organisation has a breach, some security software comes with useful tools.
Bitdefender Total Security, for instance, offers phishing and fraud protection. Norton Identity Advisor Plus includes an “identity restoration specialist” who can help a user through the process of regaining control of their identity.
Cyber incidents like the Optus breach highlight the importance of protecting individual and organisation data. Organisations are often legally responsible for protecting customer data, and the cost of an enterprise data breach is at record levels, according to IBM. The stakes have never been higher.